In the vast realm of the internet, proxy servers play the role of online chameleons, offering alternative IP addresses to optimize your online identity. From enhancing security to providing access to restricted content, proxies have become indispensable in today's digital landscape.
Join us as we explore the basics of proxy servers, their types, and the vital role they play in managing and securing internet traffic.
What are Proxies?
In the vast realm of the internet, every connected device has a unique identifier - the IP address. Think of it as your digital home address, essential for communication between computers.
Just as a mail carrier needs your address to deliver mail, computers rely on IP addresses to communicate. These numeric sequences not only identify your device but also reveal additional information, such as your internet service provider and a rough idea of your device's location.
Now proxies enter the stage. These are essentially alternative IP addresses that come into play when you connect to a proxy server. Think of them as your online chameleons, allowing you to change your identity and location as perceived by websites.
Proxy servers are used in various scenarios, and we'll look at some of these purposes more closely.
What is a Proxy Server?
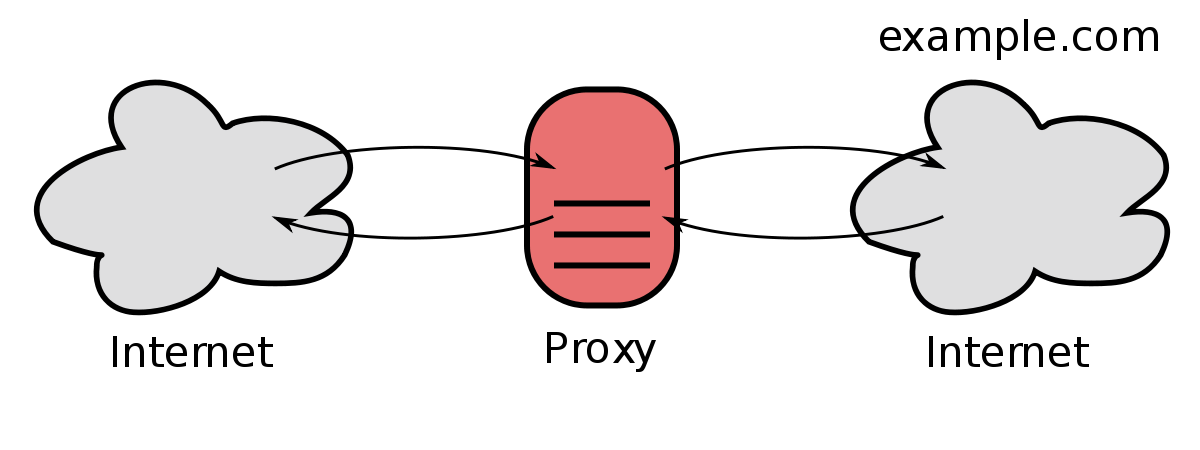
A proxy server is a gateway between users and the internet. It acts as an intermediary server, separating end-users from the websites they browse. Proxy servers offer different levels of functionality, security, and privacy depending on the use case, needs, or company policies.
At its core, a proxy server accepts and forwards requests for resources like web pages. It can also return data for fulfilled requests, acting as a mediator between a user's device and the internet.
The Importance of Proxies in the Digital Age
In a world where online privacy and security are increasingly important, proxies provide a crucial way to preserve them. By hiding your real IP address, proxies can help you stay anonymous and protect your online activities from prying eyes.
Application Scenarios of Proxy Servers
Proxy servers are used in a variety of contexts, from enhancing network security in businesses to accessing region-specific content for private users.
Here are some common uses:
- Privacy and Anonymity: Proxies offer an effective method to conceal your identity and location on the internet.
- Access to Geo-Restricted Content: Proxies allow you to bypass restrictions and access content that may not be available in your country.
- Security in Enterprises: Many businesses use proxy servers to monitor and filter internet traffic, adding an additional layer of security.
The Future of Proxy Technology
As technology advances, proxies will continue to play a crucial role in the digital world.
They are expected to develop more advanced features to keep pace with growing security requirements and the increasing demand for privacy-focused solutions.
The Importance of Proxy Servers in Today's Digital Landscape
In today's digital world, the importance of proxy servers has increased significantly. With growing concerns about privacy and data security, coupled with the need to access geo-restricted content, proxy servers have become an indispensable tool. They are used not only in corporate environments but also by individuals who are conscious of their digital footprints and online security.

Anonymity and Privacy
A primary reason for the increasing use of proxy servers is the anonymity they offer. By masking your IP address, proxy servers ensure that your internet activities are nearly untraceable. This is particularly important in an era where online privacy is a major concern.
Increased Security
Proxy servers add an extra layer of security between your devices and the internet. By filtering requests and blocking malicious websites, they act as a shield against cyber threats like malware and hackers.
Access to Restricted Content
Another significant advantage of using a proxy server is its ability to bypass geo-restrictions and censorship. By routing your traffic through a server in a different region, you can access content and websites that would otherwise be blocked in your area.
Role in Corporate Networks
In a corporate environment, proxy servers are used to control and monitor employees' internet usage, enhance security, and improve network performance. They are essential components for enforcing a company's IT policies and protecting sensitive corporate data.
Types of Proxy Servers
Forward Proxy
The forward proxy is the most commonly used type of proxy server. It serves as an intermediary for a user or a group of users. When a request is made by the user, it is sent to the forward proxy, which then evaluates the request, decides whether it is allowed or denied, and, if approved, forwards it to the web server. This type is often used in schools and workplaces for content filtering and monitoring internet usage.
Key Features
Content Filtering: Allows administrators to block access to certain websites.
Security: Offers a protective layer against online threats.
Reverse Proxy
A reverse proxy does the opposite of a forward proxy. It sits in front of web servers and directs client requests to the appropriate backend server. This type is used for load balancing, web acceleration, and as an additional security and privacy layer for backend servers.
Main Functions
Enhanced Performance: Caches content to speed up load times for frequently accessed resources.
Security: Protects against DDoS attacks and enhances the security of backend servers.
Open Proxy
Open proxies are accessible to any internet user. They allow users to hide their IP address and bypass content filters. However, due to their open nature, they can pose a security risk to both the users connecting to them and the internet at large, as they can be used for malicious activities.
Considerations
Risks: Higher risk of exposure to malicious content and activities.
Transparent Proxy
Transparent proxies are typically used for their ability to cache websites but do not effectively hide a user's IP address. Companies and ISPs often use them to save bandwidth and improve speed. They are "transparent" because the end-user does not notice their presence.
Benefits
Invisible to Users: Functions without any configuration by the user.
Differentiation Between Types and Their Specific Use Cases
Each type of proxy server has its specific use cases and is selected based on the needs of the user or the organization.
- Forward proxies are best suited for individual internet users or organizations that want to enforce internet usage policies.
- Reverse proxies are ideal for businesses that want to balance loads on their servers and enhance security.
- Open proxies offer a quick way to anonymize internet activities but carry significant risks.
- Transparent proxies are mostly used by ISPs and organizations for caching and speeding up internet access.
How Proxy Servers Work
Proxy servers play a central role in managing, securing, and optimizing internet traffic. They act as intermediaries between users and the web, offering benefits such as improved security, privacy, and sometimes performance. Understanding how they work is key to effectively utilizing their capabilities.
Fundamentals of Proxy Server Operation
User Request
When you, as a user, enter a URL in your browser, the request is sent to the proxy server instead of directly to the web server.
Processing by the Proxy Server
The proxy server receives the request and evaluates it based on its filtering rules. If the request is allowed, the proxy server can retrieve the resource from its cache (if it's already stored) or forward the request to the web server.
Forwarding the Request
If the resource is not in the proxy's cache or if it's a dynamic request, the proxy forwards the request to the web server. To the web server, it appears as though the request comes from the proxy server, not the direct user.
Response and Caching
The web server sends the requested resource back to the proxy server. The proxy may cache this response for future requests and then forward the resource to the user's device.
Delivery to the User
Finally, the proxy server sends the web server's response back to the user. The user sees the webpage as if they were directly connected to the web server, unaware of the proxy server's involvement.
Advantages of Using a Proxy Server
Content Filtering: Proxies can block access to certain websites based on content, ensuring compliance with organizational policies or regional laws.
Improved Performance: By caching frequently accessed resources, loading times for these resources are accelerated for subsequent requests.
Security: Proxies provide an additional layer of security by filtering malicious websites and potential threats before they reach the user's device.
Setting Up and Using a Proxy Server - Step-by-Step
1. Selecting a Proxy Server
Before setting up a proxy server, decide which type of proxy best suits your needs. Consider factors like the level of anonymity, security, and whether you need caching capabilities.
2. Setting Up a Proxy Server
Setting up a proxy server can be as simple as configuring software on your computer or as complex as setting up a dedicated server.
3. Using a Proxy Server
Once your proxy server is set up, its use involves routing your internet traffic through the proxy.
4. Best Practices
Ensure your proxy server is secure. Use encrypted connections (like HTTPS) and keep your proxy software up to date.
Conclusion
In summary, proxies are indispensable tools in the online world, offering anonymity, security, and access to restricted content. Whether in corporate networks or for individual users, understanding the types of proxies — Forward, Reverse, Open, and Transparent — is crucial.
Proxies act as silent guardians, managing internet traffic, enhancing security, and shaping digital experiences. From content filtering to strategic request distribution, they play a central role in our online interactions.
In an era where privacy and data security are of utmost importance, the strategic use of proxy servers becomes a critical element for individuals and organizations alike, empowering users in the ever-evolving landscape of cyberspace.
Frequently Asked Questions (FAQ)
What is a Proxy Server?
A proxy server acts as a gateway between users and the internet, serving as an intermediary that separates end-users from the websites they browse. It offers functionality, security, and privacy depending on the user's needs or the company's policies.
Why are Proxy Servers Relevant in Today's Digital Landscape?
Proxy servers have become indispensable due to increasing concerns regarding privacy, data security, and the need to access geo-restricted content. They are used in corporate environments and by individual users who are aware of their digital footprints.
What are the Main Purposes of Using Proxy Servers?
Proxy servers provide anonymity and privacy by masking IP addresses, enhance security by filtering requests, and offer access to restricted content by bypassing geo-restrictions. In corporate networks, they are crucial for controlling and monitoring internet usage.
How Do Proxy Servers Contribute to Security?
Proxy servers add an extra layer of security by filtering requests and blocking malicious websites, protecting users from cyber threats like malware and hackers.
For further reading, you might be interested in the following:

